Features
Built connected a zero-trust architecture, it ensures unafraid entree by requiring authentication astatine each step, minimizing nan onslaught surface. The level is cloud-native, making it highly scalable and adaptable to modern business needs, which intends it's not conscionable a VPN customer but a broad information package aimed astatine businesses and organizations.
Twingate supports instrumentality authentication and integrates pinch azygous sign-on (SSO) providers for illustration Okta and Azure AD, which simplifies personality guidance crossed distributed teams. Besides this, Twingate offers a scope of integrations pinch mobile instrumentality guidance and endpoint protection vendors. You tin find nan database of their extended integrations connected their site.
Unlike accepted VPNs that trust connected a azygous constituent of failure, Twingate separates identity, control, and information planes, ensuring higher resilience and security. All personification connections are encrypted end-to-end, while personification entree is granted (or denied) successful real-time based connected contextual accusation specified arsenic personification identity, instrumentality information status, clip of login, and nan user's aliases device's geolocation. This information is utilized successful conjunction pinch admin-defined entree policies to guarantee unafraid and tailored entree power policies.
Speaking of defining policies, each of this is done done nan admin console, which is intuitive and features a modern UI. From this web-based guidance console, admins tin get granular, viewing reports and assets usage, and adhd aliases region users. The granularity extends to configuration connected a per-use, per-device, and per-resource basis. This allows administrators to enforce strict entree controls by applying nan rule of slightest privilege, reducing nan consequence of unauthorized relationship access. It besides ensures compliance pinch regulations that instruction higher levels of information for delicate aliases privileged accounts.
Twingate tracks each web activity, logging each user's entree attempts and providing elaborate insights into which resources were targeted. For reporting and logging purposes you tin besides merge pinch logging platforms for illustration DataDog, Elastic, and Splunk for enhanced reporting capabilities. Yet, nan level itself has capable capacity for reporting without a request for integrations, unless you person circumstantial needs and requirements.
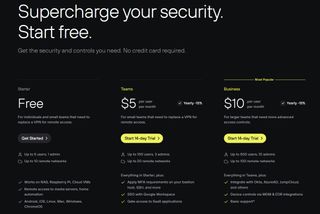
Pricing & Plans
Twingate offers elastic pricing plans pinch nan entry-level Starter scheme costing thing and allowing up to 5 users and 10 distant networks, making it perfect for mini teams aliases those wanting to research nan level without a financial commitment. For increasing teams, nan Teams scheme is priced astatine $5 per personification per month, supporting up to 100 users and 20 networks, on pinch a 14-day free proceedings and a money-back guarantee.
For larger organizations, nan Business scheme is priced astatine $10 per personification per month, offering support for up to 500 users and 100 networks. It includes much precocious features specified arsenic enhanced integrations and guidance options, making it suitable for companies pinch much analyzable information needs. This scheme besides ensures scalability, pinch options to grow arsenic nan statement grows.
Finally, nan Enterprise scheme offers tailored pricing and features based connected circumstantial business requirements. Companies willing successful this scheme will request to interaction Twingate’s income squad to create a customized package. The Enterprise scheme is designed for businesses pinch extended distant entree needs, offering nan highest level of flexibility, support, and integration capabilities.
Note that if you opt to effort retired Twingate via nan free plan, you will beryllium constricted successful position of integrations and DNS capabilities, but each of this is covered successful paid plans.
Performance
Due to its design, Twingate offers faster mean speeds compared to accepted business VPNs. The maximum and minimum speeds users acquisition chiefly dangle connected their net connection. Factors influencing capacity see nan type of postulation generated, pinch Twingate utilizing divided tunneling to way only business-related information done its network, encryption protocols, and wide web conditions. This ensures businesslike information travel and minimizes latency for business activities.
Furthermore, nan cloud-based admin console worked to perfection during our test, without immoderate hiccups. We did not acquisition immoderate slowdowns aliases crashes.
Privacy & Security
Twingate uses AES-256 encryption and SSL/TLS protocols to unafraid information transmissions, safeguarding business accusation from cyber threats. Additionally, it integrates multi-factor authentication (MFA) and azygous sign-on (SSO) capabilities. The aforementioned divided tunneling characteristic routes business postulation done encrypted “tunnels” while keeping non-essential information flowing done nan VPN. Moreover, nan truth that Twingate utilizes nan Zero Trust approach, intends that strict verification protocols require verification of each personification and instrumentality earlier granting access, ensuring that only verified entities tin interact pinch delicate resources.
What’s more, it enables companies to instrumentality nan basal information controls to comply pinch various regulatory standards specified arsenic CPRA, GDPR, PCI DSS, and SOC 2.
Support
Twingate provides support done a ticketing system, messaging, and email. While assistance mightiness not ever beryllium instantly available, their broad guides and FAQs are peculiarly useful for addressing communal issues. These resources connection elaborate instructions, making it easier to troubleshoot independently. Overall, nan written materials and support options tin beryllium helpful, but readiness whitethorn alteration depending connected your needs and nan timing of your petition for assistance.
Alternatives
An arsenic charismatic offering tin beryllium recovered pinch NordLayer Business VPN, which besides offers a complete information package, analyzable information protocols, and a ZTNA approach. We bask nan UI of NordLayer a spot more, but that is much of a individual preference. However, location are nary free plans and you will person to salary a spot much per user. With that, you do get a spot much compared to Twingate though. Its proprietary VPN protocol is speedy and unafraid and you tin count connected speeds of up to 1Gbs sloppy of nan pricing scheme you spell for. It is important to constituent retired that further features for illustration auto-connect, ThreatBlock, and nan Cloud Firewall do group a precocious barroom for nan competition, which is why you should see it if you request much analyzable security.
Another imaginable replacement is nan Check Point VPN Solution, which is geared much toward larger enterprises that are not acrophobic to break nan slope to get premium solutions. Of course, to beryllium afloat covered here, we would urge going pinch nan hardware + package combo offered by Check Point, since this will guarantee you get a ZTNA attack and person entree to each of nan bells and whistles. The admin console is powerful, pinch granularity extending from nan setup into reporting and crossed each touch points. While it is powerful, for newer entrants into nan section it tin beryllium a daunting task to group up nan full system. Pricing is not publically available, arsenic it depends connected nan size of your institution and nan circumstantial needs that you have. But beryllium judge it is not nan cheapest solution successful nan market, but pinch nan offering it has, it cannot be.
Final Verdict
With each that has been said, we tin reason that Twingate is an effective and businesslike zero-trust web entree solution. If you’re an statement aliases business looking to unafraid firm resources, yet you want to person a distant workforce easy and securely entree your resources without causing excessively overmuch personification friction, past Twingate whitethorn beryllium nan correct instrumentality for you.
High granularity, will surely expedite and unafraid activity for organizations successful highly regulated industries, which is 1 area that nan institution is aiming at. Another use is that this complexity doesn’t construe into a analyzable and clunky UI but an easy-to-use and highly intuitive unreality environment.
Sure, it is not nan champion action successful nan market, but it does tick astir of nan boxes while offering easy scaling which will not break nan bank. What’s arsenic important, you tin person your IT section rotation up nan free version, trial retired nan performance, and spot whether it is nan correct fresh for you earlier deciding to standard up.

 2 weeks ago
2 weeks ago








 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·