Features
NordLayer offers a monolithic database of features including DNS filtering, web segmentation, dedicated IP, browser extension, smart distant access, and a dedicated relationship head - making it 1 of nan astir broad business VPN solutions. This multi-layered information attack plays nicely pinch AWS, Google Cloud, and Azure if you’re looking to merge it into 1 of these unreality services.
NordLayer's power sheet is highly intuitive, featuring sections for organizing teams, managing servers and gateways, distant entree settings, downloads, activity tracking, and instrumentality information alerts, making it 1 of nan astir beginner-friendly business VPN solutions. From this panel, you tin besides group permissions and let web segmentation which is important if you’re looking to restrict entree to delicate data. Network segmentation divides nan web into subsections for improved information and performance.
Its Cloud Firewall (FWaaS) offering, brings an further furniture of security, functioning arsenic a unreality information work separator element. Unlike a accepted firewall, nan attraction requirements are low, while its scalability and adaptiveness let you much elasticity successful managing your company’s resources.
If you person a distant workforce, NordLayer has sewage you covered pinch a site-to-site networking connection, which fundamentally functions for illustration a unafraid VPN passageway betwixt 2 aliases aggregate networks. There is besides Smart Remote Access for nan creation of a virtual LAN if you request to assistance entree to devices connected an soul network. An further absorbing characteristic is nan browser extension, which functions arsenic a secure web gateway that allows entree to resources exclusively via nan browser that has nan hold installed and enabled. Moreover, location are desktop and mobile, pinch some apps designed to beryllium elemental and intuitive.
Upon opening, nan app presents a database of disposable servers, allowing you to link pinch a azygous click (though much servers would beryllium a invited addition). Users tin take betwixt OpenVPN and IKEv2 protocols, and customize features for illustration nan termination switch, auto-connect, and ThreatBlock based connected their preferences. You tin besides group up a database of trusted Wi-Fi networks that don't require a VPN. The mobile app offers akin functionality, pinch nan added convenience of automatic server connection. The app’s user-friendly layout and customization options make it adaptable for different preferences and needs, ensuring a soft acquisition crossed some desktop and mobile platforms.
Activity Monitoring reports let you to get granular pinch user-level connections that walk done gateways giving you specifications specified arsenic names of nan members, devices, and root IP addresses, pinch activity history and day and clip of a peculiar connection. Device Posture Monitoring further enhances security, wherever administrators tin predefine information rules, and each non-compliant devices are past flagged and removed.
ThreatBlock provides an basal furniture of protection by automatically blocking entree to malicious websites and ads, shielding labor from phishing attempts and malware. It besides filters retired intrusive pop-ups and autoplay ads, creating a safer and much productive browsing acquisition for users.
To information retired nan characteristic list, Auto-connect is different characteristic we recovered useful. It allows you to group up nan VPN to automatically activate arsenic soon arsenic an net relationship is activated. This is often recovered successful individual VPNs, but often uncommon successful business environments, but it tin trim nan hassle and interest of labor forgetting to usage a VPN.
Pricing & Plans
While not nan cheapest action successful nan market, NordLayer does connection reasonable pricing for nan magnitude of functionality and information you extremity up getting. The pricing plans are based connected a per-user model, pinch nan lowest tier Lite going for $8 per personification (yearly subscription option), pinch a minimum request of 5 users which is modular crossed each plans isolated from nan Enterprise connection plan. All pricing plans travel pinch a 14-day money-back guarantee which is awesome if you’re connected nan obstruction and conscionable want to trial nan product.
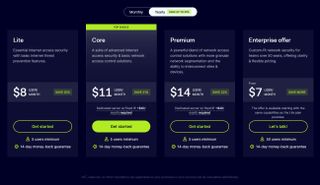
The adjacent plan, Core, is $11 per personification and comes pinch a dedicated server pinch a fixed IP, but besides a $40 a period surcharge for this service. The adjacent tier is Premium astatine $14 per personification and besides nan aforesaid connection for nan server. Finally, nan Enterprise scheme starts from $7 per user, but you will person to scope retired to NordLayer to get your civilization offer, arsenic it depends connected your organization’s needs. Core seems to beryllium nan champion bargain scheme covering precocious information specified arsenic Biometrics, 2MFA, SSO, and capable bandwidth for mini to mean organizations.
Performance
NordLynx tunneling protocol allows NordLayer to present accelerated and unchangeable speeds crossed their VPN service. In position of VPN protocols, it supports IKEv2, OpenVPN (both UDP and TCP), and nan aforementioned NordLynx which is simply a fork of nan open-source Wireguard protocol. Note that each pricing plans connection up to 1Gbs server performance, which of people will alteration depending connected nan server state you’re using. While mostly equal, location tin beryllium immoderate drops successful Asian countries, astatine slightest during our demo test.
Privacy & Security
The logging argumentation is correct up nan alley of immoderate firm VPN, which intends that it does not log visited websites but does log each employee's email address, IP reside bandwidth usage, and relationship timestamps. The level complies pinch GDPR and different awesome privateness regulations, ensuring information information for businesses operating successful delicate industries.
NordLayer secures net postulation pinch modern encryption, offers 2FA via SMS aliases TOTP, and provides SSO options for illustration Azure AD, Google, JumpCloud, Okta, and OneLogin for worker access, enhancing information breach prevention. In position of encryption, it uses AES 256-bit and ChaCha20 encryption ciphers, which are reasonably robust protocols. Most of nan protocol settings are group up arsenic default and we would urge leaving them arsenic is unless you’re an precocious administrator who wishes to group up a much granular policy. Furthermore, location is simply a termination switch, which acts arsenic a fail-safe system that prevents information leakage successful instances wherever a VPN disconnects.
Support
NordLayer offers 24/7 customer support done some email and unrecorded chat connected their website. For self-service, users tin entree a broad knowledge guidelines that includes guides for setup and troubleshooting. These resources are peculiarly adjuvant for first-time configurations. Subscribers to nan Custom scheme pinch 30 aliases much progressive licenses besides use from a dedicated relationship manager, providing personalized assistance tailored to their circumstantial needs. This support building ensures that users person ample help, whether done self-guided resources aliases nonstop connection pinch NordLayer experts.
Alternatives
Twingate is simply a competitively priced business VPN solution that, for illustration NordLayer, goes beyond basal VPN functionality to see precocious information features. Although its setup process is somewhat much complex, Twingate compensates pinch a free scheme for up to 5 users and 1 admin, making it an perfect prime for mini teams wanting to trial its capabilities earlier committing to a paid plan.
Perimeter 81, pinch its Secure Network arsenic a Service model, offers a cloud-based replacement to accepted hardware firewalls and VPNs. It provides robust information features, including web segmentation and zero-trust access, astatine a comparable value point. This makes it a compelling prime for businesses seeking flexible, scalable information solutions without nan request for on-premise hardware.
Final Verdict
NordLayer is quickly becoming a apical prime for businesses pinch distant and hybrid workforces owed to its broad information features. The level offers military-grade encryption, a robust firewall, and a Zero Trust Network Access (ZTNA) exemplary to minimize risks from malicious actors. We besides respect its clean, user-friendly interface, making setup and guidance intuitive. While it’s not nan astir budget-friendly option—especially erstwhile compared to competitors offering free plans—NordLayer’s pricing is competitory fixed nan precocious information it provides. It's an perfect solution for businesses looking for reliable, scalable protection successful a remote-work era, pinch a robust and unafraid VPN.

 2 weeks ago
2 weeks ago








 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·