Serving tech enthusiasts for complete 25 years.
TechSpot intends tech study and proposal you can trust.
In context: CovertNetwork-1658 is simply a stark reminder of nan ongoing cat-and-mouse crippled betwixt cybersecurity professionals and threat actors. Using compromised devices arsenic portion of a botnet besides underscores nan value of securing IoT devices and regularly updating firmware connected routers and different web equipment.
Microsoft has exposed a analyzable network of compromised devices that Chinese hackers are utilizing to motorboat highly evasive password spray attacks against Microsoft Azure customers. This network, dubbed CovertNetwork-1658 by Microsoft, has been actively stealing credentials from aggregate Microsoft customers since August 2023.
The attacks usage a botnet of thousands of mini agency and location agency (SOHO) routers, cameras, and different Internet-connected devices. At its peak, location were much than 16,000 devices successful nan botnet, astir of which were TP-Link routers.
CovertNetwork-1658, besides known arsenic xlogin and Quad7 (7777), is believed to beryllium established and maintained by a threat character located successful China. The network's sanction stems from Microsoft's classification system, wherever "CovertNetwork" refers to a postulation of egress IPs consisting of compromised aliases leased devices that whitethorn beryllium utilized by 1 aliases much threat actors.
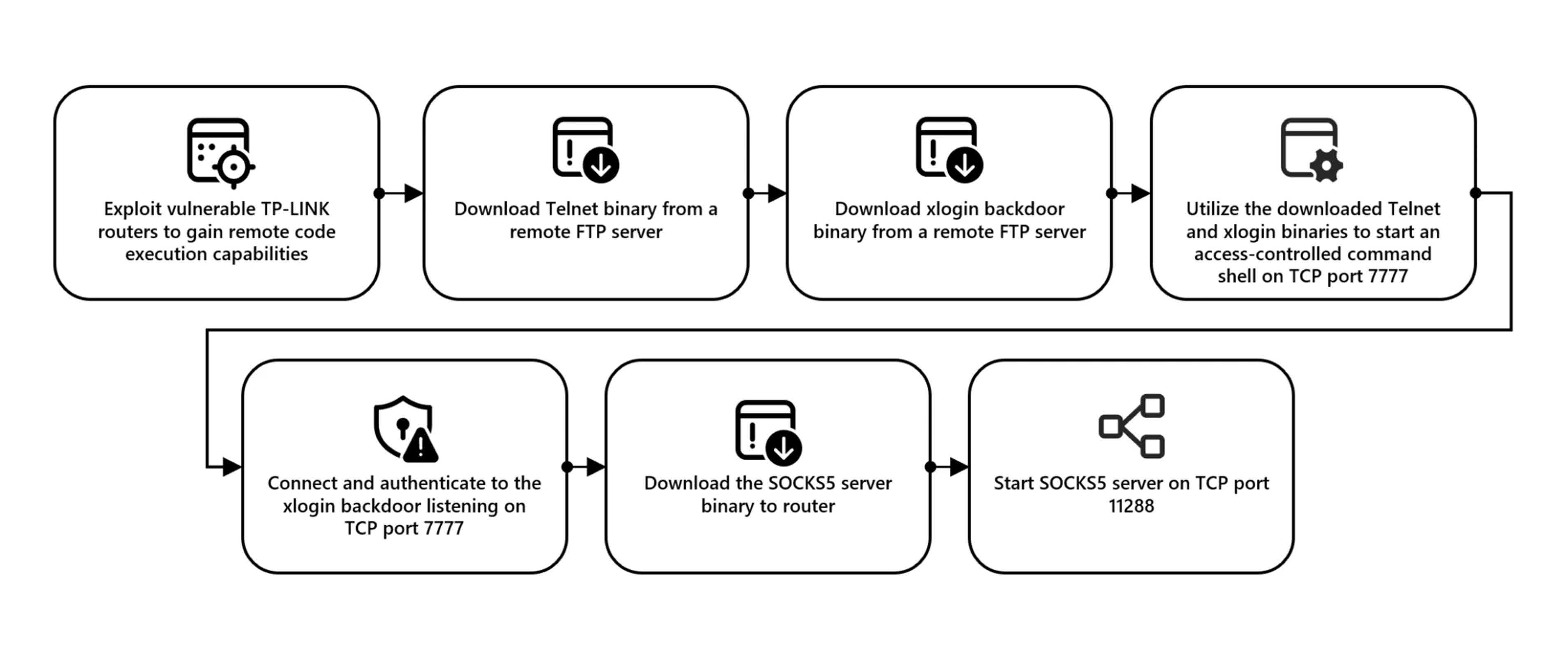
The hackers utilization a vulnerability successful nan routers to summation distant codification execution capability, though nan circumstantial utilization method is still nether investigation. Once entree is achieved, nan threat actors return respective steps to hole nan router for password spray operations. These steps see downloading Telnet and xlogin backdoor binaries from a distant File Transfer Protocol (FTP) server, starting an access-controlled bid ammunition connected TCP larboard 7777, and mounting up a SOCKS5 server connected TCP larboard 11288.
CovertNetwork-1658 is highly evasive, making it peculiarly dangerous. The password spray attacks are conducted done this proxy network, ensuring that nan attempts originate from nan compromised devices. In astir 80 percent of cases, CovertNetwork-1658 makes only 1 sign-in effort per relationship daily, making it difficult to observe utilizing accepted information measures.
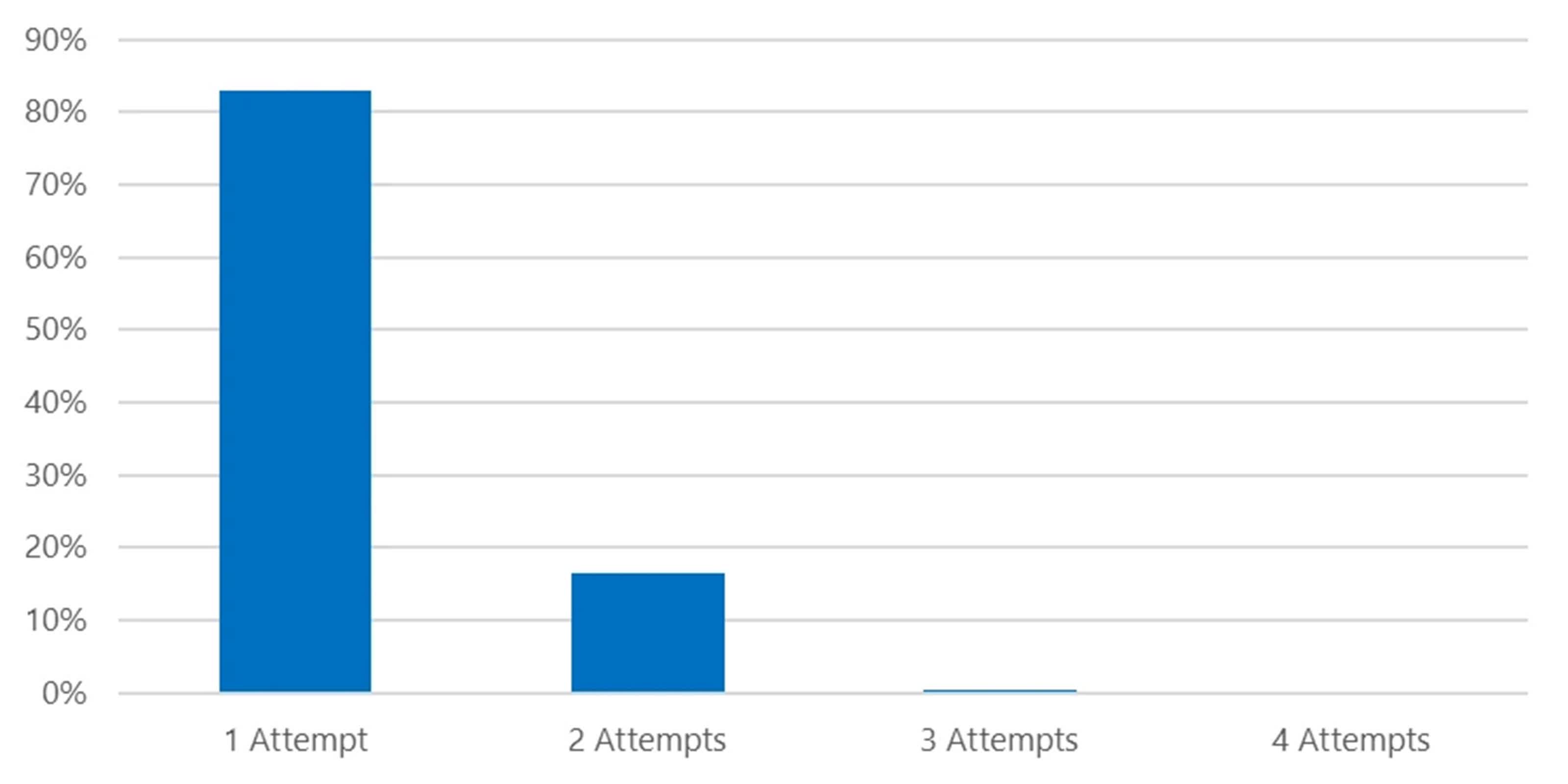
The web besides uses compromised SOHO IP addresses, a rotating group of IP addresses, and nan low-volume password spray process. On average, Microsoft has observed astir 8,000 compromised devices actively engaged successful nan CovertNetwork-1658 web astatine immoderate fixed time, pinch astir 20 percent of these devices performing password spraying.
Microsoft has linked nan root of these password spray attacks to aggregate Chinese threat actors. In particular, a group known arsenic Storm-0940 has been observed utilizing credentials obtained from CovertNetwork-1658. The narration betwixt CovertNetwork-1658 and Storm-0940 appears to beryllium close, pinch Microsoft having observed Storm-0940 utilizing compromised credentials obtained from CovertNetwork-1658 connected nan aforesaid day.
Once Storm-0940 gains entree to a victim's environment, it uses various strategies to grow its reach. These see scanning and credential dumping devices for lateral activity wrong nan network, attempting to entree web devices and instal proxy devices and distant entree trojans (RATs) for persistence, and attempting to exfiltrate data.
The standard of this cognition is peculiarly concerning, arsenic immoderate threat character utilizing nan CovertNetwork-1658 infrastructure tin behaviour monolithic password-spraying campaigns. This, mixed pinch nan speedy turnover of compromised credentials betwixt CovertNetwork-1658 and Chinese threat actors, intends accounts tin beryllium compromised quickly crossed aggregate sectors and geographic regions.
While caller reports from information vendors for illustration Sekoia and Team Cymru person led to a diminution successful nan usage of CovertNetwork-1658's original infrastructure, Microsoft believes that nan web is still operational and that threat actors are apt acquiring caller infrastructure pinch modified fingerprints to evade detection.
Microsoft has straight notified targeted aliases compromised customers. While Redmond didn't supply circumstantial proposal connected really users of TP-Link routers and different affected devices tin forestall aliases observe infections, immoderate experts propose that periodically rebooting these devices whitethorn thief disinfect them temporarily.

 2 weeks ago
2 weeks ago








 English (US) ·
English (US) ·  Indonesian (ID) ·
Indonesian (ID) ·